How to implement Smart Card Logon with ReTrust.Me
Step 1: Prepare the environment
- Install ReTrust.Me. Don't type in an admin password, in order to select certificate authentication. Select RSA cryptosystem (with or without HSM).
- Perform the Key Ceremony within ReTrust.Me, that is: generate the CA
- Download the generated CA certificate (from the CA Management section)
- Generate at least one operator using the appropriate menu, and save the .p12 file
Step 2: Enroll Active Directory in the PKI
- Using the CA certificate (ca.crt) downloaded in 1.3, run as administrator with "Enterprise Admins" rights:
certutil -dsPublish -f c:\path\to\ca.crt RootCA
certutil -dsPublish -f c:\path\to\ca.crt NTAuthCA
gpupdate /force
- Download DCEnrollment.exe (sha1sum: 63a39d3ad9dac72015cb2c95317e41ec293904de)
- On each Domain Controller, execute DCEnrollment.exe as admin and follow the instructions in order to sign the CSR from ReTrust.Me PKI, and import it in the DC
Step 3: Prepare the Active Directory domain
- Declare a new "Registry" GPO, by launching gpedit.msc and going to "Computer Management" > "Preferences" > "Windows Settings" > "Registry", and add a new Registry entry:
- Action: Update
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Microsoft Base Smart Card Crypto Provider
- Value Name: AllowPrivateExchangeKeyImport
- Value type: REG_DWORD
- Value data: 00000001
- Declare a new "Smart Card" GPO, by launching gpedit.msc and going to "Computer Configuration" > "Policies" > "Administrative Templates" > "Windows Components" > "Smart Card":
- Double click on "Allow Integrated Unblock Screen to be displayed at the time of logon
- Select "Enabled" and save your changes
Step 4: Enroll the users
- On a workstation, import the operator certificate generated in 1.4
- Download the EnrollmentClientInstaller.exe from the PKI's "CA Management" section, and install it with following parameters:
- URL will be https:// followed by the DNS FQDN name of your PKI and by "/crmp"
- Profile: scl_cert
- Select the operator certificate imported in 4.1 from the displayed list
- Launch the Enrollment Client from the Windows menu
- Then, for each user, insert a blank card/token (or recycle one using the "Format" button), fill in CN with his name, and Mail/UPN with the user's MSUPN (generally windowslogin@domain), have the user fill in a PIN, and press "Enroll"
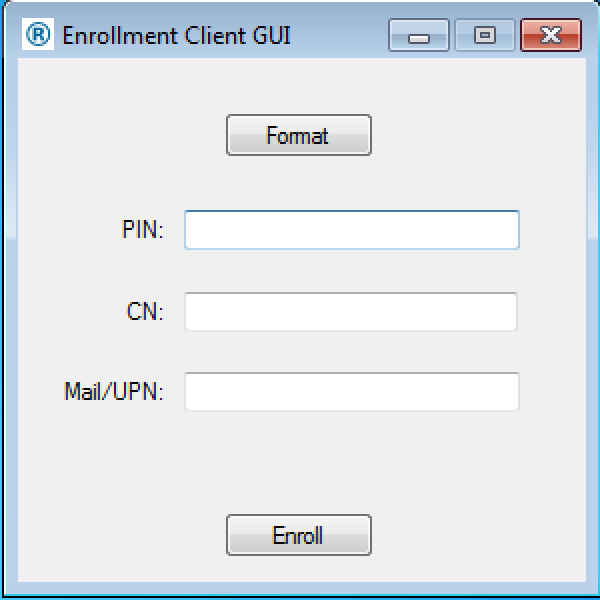
- General Note: you do not need to be administrator to perform the steps in this "Step 4" section
- VSC Note: for VSC enrollment, activate the Roaming Profile for the operator, and on each machine launch: "tpmvscmgr.exe create /AdminKey PROMPT /generate". When prompted, enter 000000000000000000000000000000000000000000000000 . Then perform the enrollment as above.
Unblocking a smart card
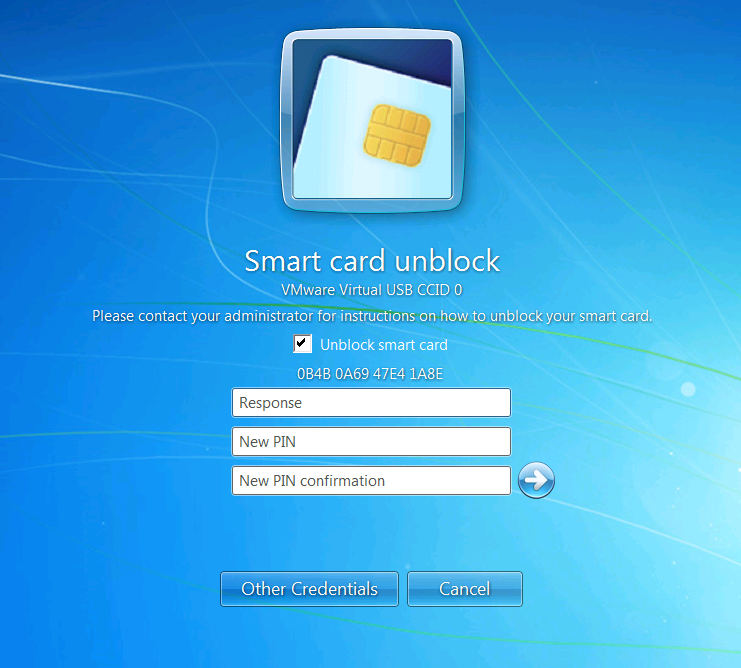
When a SmartCard is blocked, Windows offers a standard dialog to unblock it. To use it:
- Press control-alt-delete on an active session. Click on “Change a password”.
- Click on “Other Credentials”, and select the SmartCard reader.
- Check the box "unblock smart card"
- Retrieve the challenge (0B4B 0A69 47E4 1A8E in the example below), and hand it over to a PKI operator
- The PKI operator types in the challenge in the "Challenge" field of the "Unblock Smart Card" entry in the "CA Management" section, and gives back the Response
- Fill in the response and the new PIN, and validate: the SmartCard is unblocked!
References and useful tools

